I’ve talked on several occasions about how we can easily use the SharePoint 2010 object model (OM) to discover who has access to a securable object (SPWeb, SPList, or SPListItem) and the fact that we can use the same mechanisms within PowerShell to create useful security/audit reports. On some of those occasions I’ve shown a version of a PowerShell script which gives you a dump to the screen or a text file of every securable object and who has access to it and how they were given access to it – today I’d like to share a new version of that script.
Before we get to the actual script let’s first talk about how to get the information. All securable objects have a method named GetUserEffectivePermissionInfo which is defined in the abstract base class SPSecurableObject (in 2007 this method was defined directly on the SPWeb, SPList, and SPListItem objects). This method returns back an SPPermissionInfo object which we can use to inspect the various role definition bindings and corresponding permission levels.
Once we have the permission details we simple loop through the SPRoleAssignments objects via the RoleAssignments property. This will give us information about how the user is given access to the resource. Next we look at the RoleDefinitionBindings property which returns back a collection of SPRoleDefinition objects that tell us about the type of access granted (e.g., Full Control, etc.).
I then take all this information, stick it in a hash table which I then use to create a new object which gets written to the pipeline.
So with that, let’s take a look at the code:
Great – we’ve got the code – so now you’re probably asking, “how the heck do I use it?” Well the first thing you need to do is save it to a file, let’s call it SecurityReport.ps1 and we’ll put it in the root of the C drive. Once saved we can load it in memory using the following:
1C:\ PS> . .\SecurityReport.ps1
Now for the fun stuff :). The examples I’m going to show will build off of each other and will eventually conclude with an example that gives me a report for all users and all securable objects throughout the entire farm. The first example I want to show is how to retrieve a report for a single user and a single web (we’ll reuse the $user variable throughout the script so I’ll only define it once here):
1$user = "sp2010\siteowner2"
2Get-SPWeb "http://portal" | Get-SPUserEffectivePermissions $user | Out-GridView -Title "Web Permissions for $user"
Running this command will generate a grid view as shown here:
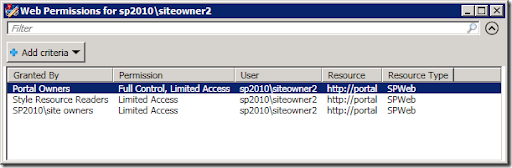
Note that I could have just as easily saved the results to a CSV file which I could then open in Excel using the Export-Csv cmdlet:
1Get-SPWeb "http://portal" | Get-SPUserEffectivePermissions $user | Export-Csv -NoTypeInformation -Path c:\perms.csv
For this next example I’m going to show the permissions for the same user for ALL webs throughout the entire farm (note that this won’t include lists or items):
1Get-SPSite -Limit All | Get-SPWeb | Get-SPUserEffectivePermissions $user | Out-GridView -Title "All Web Permissions for $user"
Now I want to get the permissions for the same user for all lists throughout the entire farm:
1Get-SPSite -Limit All | Get-SPWeb | %{$_.Lists | Get-SPUserEffectivePermissions $user} | Out-GridView -Title "List Permissions for $user"
Now we’re going to get nice and deep and show the permissions for every single item throughout the entire farm (probably don’t want to run this on any front-end servers):
1Get-SPSite -Limit All | Get-SPWeb | %{$_.Lists | %{$_.Items | Get-SPUserEffectivePermissions $user}} | Out-GridView -Title "Item Permissions for $user"
So now that I’ve shown you how to get the individual securable objects results throughout the farm for a single user let’s now go ahead and stitch them together into one report:
1Get-SPSite -Limit All | ForEach-Object {
2 $site = $_
3 $webPermissions += $site | Get-SPWeb –Limit All | Get-SPUserEffectivePermissions $user
4 $listPermissions += $site | Get-SPWeb –Limit All | %{$_.Lists | Get-SPUserEffectivePermissions $user}
5 $itemPermissions += $site | Get-SPWeb –Limit All | %{$_.Lists | %{$_.Items | Get-SPUserEffectivePermissions $user}}
6 $site.Dispose();
7}
8$webPermissions + $listPermissions + $itemPermissions | Out-GridView -Title "Web, List, and Item Permissions for $user"
In this example I’m simply performing the same calls but appending to an array of objects and then dumping the combination of those arrays to the grid. Note that in this case I’m calling $site.Dispose() but below I’ll be using the SPAssignmentCollection to dispose of objects – keep reading for an explanation.
So now lets take it one step further and see how we can get the same reports but this time for every user. We’ll start with webs again – in this example we’ll get the permissions for all users for a given site:
1$gc = Start-SPAssignment
2$site = $gc | Get-SPSite "http://portal"
3$site | Get-SPWeb –Limit All | Get-SPUserEffectivePermissions ($site.RootWeb.SiteUsers | select LoginName) | Out-GridView -Title "Web Permissions for All Users In $($site.Url)"
4$gc | Stop-SPAssignment
As you can see I’m basically using the SiteUsers property from the root web and passing the login name for each user into the function. Note that here I’m using the Start-SPAssignment and Stop-SPAssignment cmdlets – that’s because I’m using the SPSite object after the pipeline execution finishes (as opposed to the above) so I need to make sure it gets disposed (I could just as easily called Dispose on the object as I did above but I’m attempting to demonstrate when/why you’d use the assignment collections).
Now lets see the lists:
1$gc = Start-SPAssignment
2$site = $gc | Get-SPSite "http://portal"
3$site | Get-SPWeb –Limit All | %{$_.Lists | Get-SPUserEffectivePermissions ($site.RootWeb.SiteUsers | select LoginName)} | Out-GridView -Title "List Permissions for All Users in $($site.Url)"
4$gc | Stop-SPAssignment
Starting to see a pattern? Let’s take a look at the list items now:
1$gc = Start-SPAssignment
2$site = $gc | Get-SPSite "http://portal"
3$site | Get-SPWeb –Limit All | %{$_.Lists | %{$_.Items | Get-SPUserEffectivePermissions ($site.RootWeb.SiteUsers | select LoginName)}} | Out-GridView -Title "Item Permissions for All Users in $($site.Url)"
4$gc | Stop-SPAssignment
Great! So now lets piece this last bit together so we can see the permissions for all webs, lists, and list items for every user within a single site collection:
1$gc = Start-SPAssignment
2$site = $gc | Get-SPSite "http://portal"
3$webPermissions = $site | Get-SPWeb –Limit All | Get-SPUserEffectivePermissions ($site.RootWeb.SiteUsers | select LoginName)
4$listPermissions = $site | Get-SPWeb –Limit All | %{$_.Lists | Get-SPUserEffectivePermissions ($site.RootWeb.SiteUsers | select LoginName)}
5$itemPermissions = $site | Get-SPWeb –Limit All | %{$_.Lists | %{$_.Items | Get-SPUserEffectivePermissions ($site.RootWeb.SiteUsers | select LoginName)}}
6$webPermissions + $listPermissions + $itemPermissions Out-GridView -Title "Web, List, and Item Permissions for All Users in $($site.Url)"
7$gc | Stop-SPAssignment
Alright, we’re almost done – let’s now stitch this all together and generate a single report showing all permissions for all securable objects (webs, lists, and list items) for every user within every site collection:
1Get-SPSite -Limit All | ForEach-Object {
2 $site = $_
3 $webPermissions += $site | Get-SPWeb –Limit All | Get-SPUserEffectivePermissions ($site.RootWeb.SiteUsers | select LoginName)
4 $listPermissions += $site | Get-SPWeb –Limit All | %{$_.Lists | Get-SPUserEffectivePermissions ($site.RootWeb.SiteUsers | select LoginName)}
5 $itemPermissions += $site | Get-SPWeb –Limit All | %{$_.Lists | %{$_.Items | Get-SPUserEffectivePermissions ($site.RootWeb.SiteUsers | select LoginName)}}
6 $site.Dispose();
7}
8$webPermissions + $listPermissions + $itemPermissions | Out-GridView -Title "Web, List, and Item Permissions for All Users in All Sites"
Note in this last example, as I did previously when looping through all site collections, I’m calling the Dispose() method inside the ForEach-Object script block. I do this because objects wouldn’t otherwise get disposed until the pipeline execution has finished and because it’s continuing to iterate so the pipeline has not yet completed. If I used the assignment collection I wouldn’t get a disposal until after I’m done iterating which would be too late – I want to dispose right when I’m done with the individual SPSite objects to avoid out of memory errors.
Reporting on who has access to what is one of the things I get asked about most frequently so hopefully this code sample and corresponding examples will prove to be useful to people. One possible area of improvement to the script would be to accommodate groups being passed in – right now I’m only considering users; and of course you could easily turn the example usages into functions. As always, if anyone has any feedback (bugs, improvements, etc.) please post here so that myself and others may benefit.
